- Binary Arithmetic, truth tables and circuit diagrams.
- Linux project using SSH to access an Amazon Web Services virtual machine
- Shell Scripting tasks

|
|

|
This is an overview of the final assignment for the Computer Architecture and Technology Convergence Assignment module. The module aimed to provide an introduction to the internal workings, structure, architecture and organisation of modern computer architectures including topics on computer hardware, abstraction, problem solving and communications.
This module looked at the mechanics of hardware that underlie any software developments, at the bits and pieces that makeup a computer system and getting an overview of how they work. It also looked at the convergence of technology and how the growing prevalence of the cloud and internet is connecting us in ways that we haven’t always seen before.
The assignment consisted of various topics.
-
Binary arithmetic, truth tables and circuit diagrams.
-
Linux assignment - working on a Linux terminal on an Amazon Web Services using Secure Shell (SSH).
-
Shell scripting
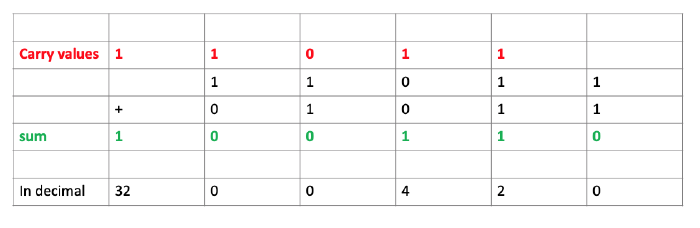
Q1.1 Add 11011 to 1011
My answer in binary is 0100110 The decimal equivalent is 38.
(0 *1 + 1*2 + 1*4 + 0*8 + 0*16 + 1*32= 2 + 4+ 32 = 38)
11011 in binary is 27 in decimal 1011 in binary is 11 in decimal 27 +11=38
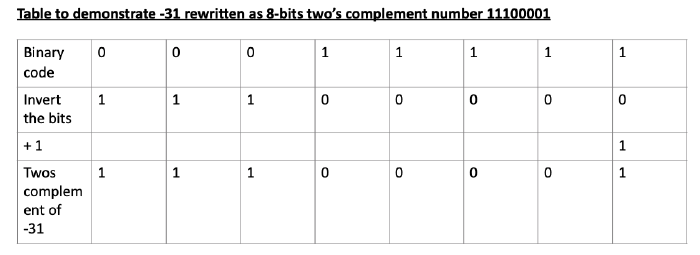
Q1.2 Rewrite the following base-10 numbers as 8-bit two’s complement numbers: -31 & 59
Using binary numbers to store negative numbers is called Two’s complement. All numbers are stored as positive binary numbers, but half are encoded to be interpreted as negaTve. First find the equivalent absolute value in binary so here find the binary equivalent of 31 and 59. Then invert all the bits and add 1, with a carry if required.
-31
31 in base 10 is 11111 in base 2 or 00011111
00011111 equivalent to 31 in decimal
11100000 flipping or inverting all the digits
Add 1
Answer: 11100001 is the Two’s complement of –31 in 8 bits
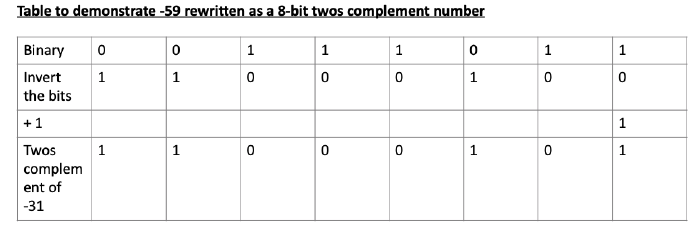
111011 (111011 = 1 + 2+0 +8+16+32 = 59)
00111011 8 bits
11000100 inverting all the bits
Adding 1
Answer 11000101 is the Two’s complement of –59 in 8 bits
Q1.3 What does the bit pattern 11101001 represent if you interpret it as an 8-bit two’s complement integer?
For zero and all positive numbers the ledmost bit is zero. For negative numbers the leftmost bit is always 1 so the number here is a negative number.
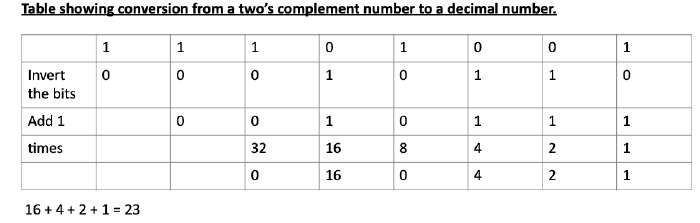
16 + 4 + 2 + 1 = 23
As it is a negative number, the answer is -23
Could also reverse the steps of going from decimal to two’s complement and this gives the same result.
Subtract 1 from the number given, then invert the result of this.
Then convert the number to decimal ignoring the first bit which indicates that the number is a negative number.
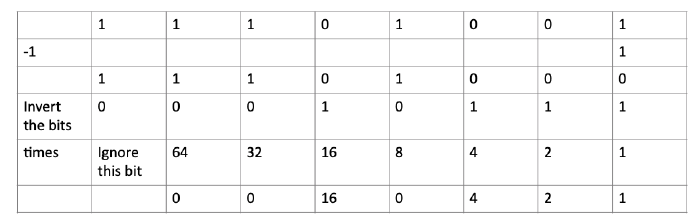
11101001 represents the decimal number –23
Answer: The bit pattern 11101001 represents -23 in decimal if you interpret it as an 8-bit two’s complement integer
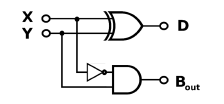
Q1.4 Draw up the truth table for the circuit shown.
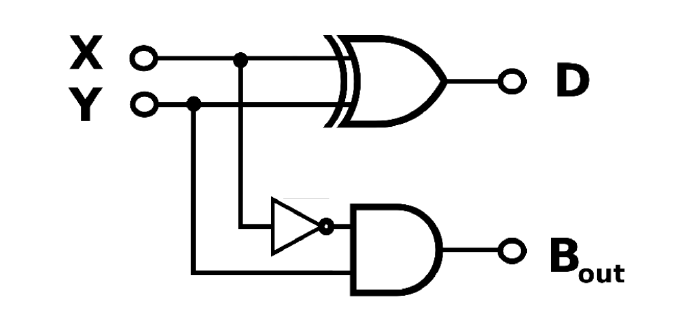
B = X’Y. Input X is inverted, then ANDed with Input Y to produce Output B.
A NOT gate takes one input signal and return the opposite signal as the output.
If a NOT gate accepts a 0, it outputs a 1
if a NOT gate accepts a 1, it outputs a 0
AND gate takes two input signals. AND gate outputs a 1 only when both inputs are high (1) and in all other cases outputs a 0.
Here Input X is inverted, then ANDed with input Y to get Output B
XOR Gate takes two input signals. If the inputs are not in agreement the output is 1. Otherwise the output is zero. Here X is XORed with Y to get output D
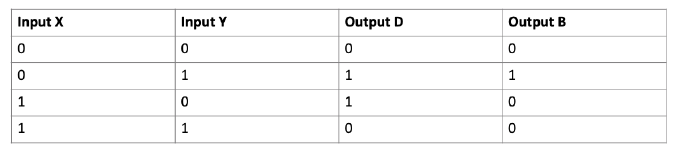
This circuit looks quite like a half adder circuit but with a NOT gate into the carry value. I would think the opposite then of a half adder, maybe a half subtractor!?
A half adder is a circuit that computes the sum of two bits and produces the correct carry bit. The carry is only 1 when both inputs X and Y are 1 as 1 + 1 = 10 in base 2.
Without the NOT gate, output D would be the sum and output B would be the carry.
With the NOT gate, the opposite of the carry would be the borrow.
There would only be a carry/ borrow value for the subtracTon of 1 from 0. In the truth table above, this is when X is 0 and Y is 1 for 0 –1.
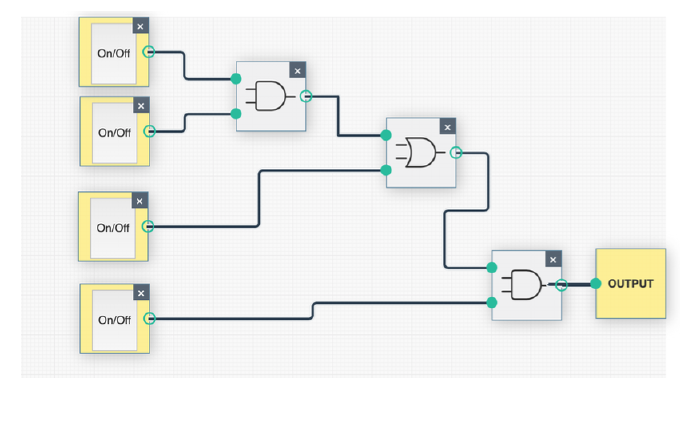
Q1.5 Draw the circuit diagram for the Boolean logic equation: (AB + C)D
Q2 Linux assignment
Enter selected commands into the Linux Terminal on the AWS VM. In your own words, write a brief description of what each command does.
echo hello worldpasswddate*hostname*archuname -a*dmesg | more(you may need to press q to quit)uptime*whoami*who*lastfinger*w*top* (you may need to press q to quit)echo $SHELLecho {con,pre}{sent,fer}{s,ed}man ls(you may need to press q to quit)man whoclearcal 2000cal 9 1752yes please(you may need to press Ctrl-c to quit)time sleep 5history*
For each of the commands marked with an *, group them into a shell script so that you can automate execution of the commands. Write the shell script using the Vim text editor. Once you have verified that the script works, add output redirection to append the output of each command to a file named as follows: firstnameSurname.txt (replacing firstname and surname with your own details). When writing to this text file, make liberal use of the echo command within the shell script to format the output nicely – i.e. insert blank lines or other demarcations and headings to make your file easily readable.
-
echo hello worldprints or displays the string ‘hello world’ to the screen.echowrites the argument following it to the standard output. -
passwdcommand changes or creates passwords for user accounts. A normal user can only change the password for their own account while the superuser can change the password for any account. -
datecommand displays the current date and time. It displays the system time and date and can be also used to set the system time and date using further arguments. -
hostname(on its own) prints the name of the current host system. It displays the current host and domain names of the current machine. A host is a computer that is connected to the network. The hostname is a name assigned to the host to uniquely identify it on the network so that it can be addressed without using its full IP address. Using hostname on the virtual machine I got ip-172-31-35-93 -
archcommand without any arguments prints the machine’s architecture type or machine hardware name On the virtual machine, the arch command printed the machine’s architecture type which is x86_64 which is a 64-bit x86 CPU architecture. -
uname –acommand prints some system information. On the virtual machine the commanduname -areturns the following information:
Linux ip-172-31-35-93 4.4.0-1075-aws #85-Ubuntu SMP Thu Jan 17 17:15:12 UTC 2019 x86_64 x86_64 x86_64 GNU/Linux The kernel name is Linux, the network node hostname ip-172-31-35-93, the release version number 4.4.0-1075-aws, the kernel version #85-Ubuntu SMP Thu Jan 17 17:15:12 UTC 2019, the machine hardware name x86_64, the processor type x86_64,the hardware platorm x86_64 and the operaTng system GNU/Linux
-
dmesg | moreHere, the result of thedmesgcommand is piped using the pipe operator|into themorecommand. Themorecommand is a filter to allow the user to page through the text one screen at a time. Thedmesgprints the kernel messages to the screen by default. The kernel is the core of the operating system and the first part of the OS that is loaded into memory when the computer starts up. The messages generated by the kernel show the hardware devices that the kernel detects and whether it can configure them. The messages come from the kernel ring buffer. All the messages from the kernel ring buffer are displayed on the screen by default. When the result ofdmesgis piped into themorecommand allows the user to page through the text of the kernel ring buffer messages one screen at a time. -
The
uptimecommand shows how long the system has been up and running. It shows the current time, how long the system has been running for, how many users are currently logged in and the system load averages for the past 1, 5 and 15 minutes. The system load averages are the average number of processes that are either in a runnable (using or waiting to use the CPU) or uninterruptable state (waiting for I/O access). Theuptimecommand shows here that the system has been running for 29 days, 4 hours and 35 minutes, there are 7 users currently logged in and the system load averages are zero. There are no processes currently in a runnable or uninterruptable state. The results when I first ran the command showed: 15:21:52 up 29 days, 4:35, 7 users, load average: 0.00, 0.00, 0.00 The most recent Tme when I ran the command shows. 18:32:37 up 43 days, 7:46, 17 users, load average: 0.00, 0.00, 0.00 Showing that the system has been running for 43 days, 7 hours and 46 minutes, there are currently 17 users logged in and again the system load averages are zero. -
whoamiprints the username of the person running the command. It shows the name you are logged in under. When I run it I get my own username. Thewhoamicommand prints the current name associated with the current effective user id -
whocommand shows the name of the users that are currently logged in plus their tty name (the native terminal device – the file name of the terminal that is connect to the standard input which in my case is the keyboard), login dates and times and terminal id’s, and the ip address of the user. -
lastcommand shows the users that were last logged in and their ttys with the most recent users logged in listed first. It gives the username, the pty ( the pseudo terminal device ) they are logged into, their IP address, the time and date they last logged in, and the time they logged out if they have logged out or else it will show if they are still logged in. -
fingeris a user information lookup program which displays information about the system users, including the user’s login name, real name if available, terminal name, write status, idle time, login time, location or ip address and phone number if the information is available. -
The
wcommand shows the current activity on the machine - who is logged in and what they are doing on the machine. It shows their username, terminal, IP address, time they logged in at, the JCPU time (time used by all processes attached to the tty including currently running background jobs), the PCPU which is the time used by the current process and the name of their current process. It also shows the current time of day, how long the system has been running, the number of users logged in and the system load averages – the average number of active processes active during the last 1, 5 and 15 minutes, where a process is a running instance of a program. -
The
topcommand displays Linux processes. It shows the Linux processes that are currently running. It provides a dynamic real-time view of a running Linux system including system summary information, the list of processes or threads currently being managed by the Linux kernel. It also shows who is logged in, how long the system has been up and running, how many tasks are currently running, the load averages, information about the CPU and memory. -
The
echocommand sends input strings to the standard output, that is it displays text to the screen. The commandecho $SHELLshows which shell will be executed by login when you log in. It shows the default shell or the value of the SHELL environment variable. The default shell in the virtual machine we are logging into is the bash shell (Bourne Again Shell) -
The command
echo {con,pre}{sent,fer}{s,ed}is a shell expansion command or a brace expansion method which is a way to generate arbitrary strings. The strings contained in the first curly braces{con, pre}are combined with the strings in the next curly braces{sent, fer}and the strings in the third curly braces{s, ed}to create strings. The result is then printed to the screen. Three sets of braces with two possible strings in each brace produces 8 possible combination of the strings. The combinations work from left to right.
echo {con,pre}{sent,fer}{s,ed} outputs the following:
consents consented confers confered presents presented prefers preferred
-
The command
man lsprints the online manual pages for thelscommand. Thelscommand is the command to show the list of files in the current directory. The commandman lsprints the name of thelscommand, a brief synopsis of the command and a description of what thelscommand does. It also shows the optional parameters that can be provided to thelscommand and what these do. -
The command
man whoprints the online manual pages for thewhocommand. Thewhocommand displays who is logged into the system.man whoprints the name of themancommand, a synopsis of the command, and a description of what thewhocommand does. It also shows the optional parameters that can be provided to thewhocommand and what these do. -
clearcommand clears the terminal screen of the previous commands. -
cal 2000command displays a calender for the year 2000. -
cal 9 1752command displays a calender for the month of September 1752
September 1752
Su Mo Tu We Th Fr Sa
1 2 14 15 16
17 18 19 20 21 22 23
24 25 26 27 28 29 30
The calendar is missing the days from the 3rd to the 13th September! This was due to the changeover from the Julian calendar to the Gregorian calendar in Britain in 1753. The Gregorian calendar was introduced in 1582 by Pope Gregory XIII but was not adopted by Britain until 1753. It includes a leap year every 4 years that allows the year to correspond closely with the astronomical year. Over time the Julian calendar fell out of line with the seasons and was less accurate than the gregorian calendar so when Britain changed from using the Julian calendar to using the Gregorian calendar in 1752 the 3rd September became the 14th September!
-
The command
yes pleaserepeatedly outputs the string ‘yes’ to the screen until it is killed. By default, the commandyeson its own will outputyfor yes. You have to pressctrlandcto exit. The reasons to use this command might be to avoid having to type ‘yes’ or confirm certain operations that ask for a ‘y’ or ‘yes’ or to test high loads of CPU on a system. -
The command
time sleep 5runs the sleep command for 5 seconds and then outputs a summary of the system resources used by thesleepcommand. Thetimecommand executes and times the utility command that comes after it. Thetimecommand runs a program or command and produces a summary of the system resource used by that command. When the utility command finishes, the time command displays information about the resources used by the command. Thesleepcommand causes a delay for a specified amount of time. It pauses or suspends execution for the time specified with the default being for seconds.sleep 5would cause a delay or pause for 5 seconds. After thesleepcommand finishes,timewrites the total time elapsed, the time consumed by system overhead and the time used to execute the command to the standard error stream. Times are reported in seconds. -
The
historycommand outputs the history of the current user to the screen. The output is numbered with the older commands at the top and newer commands at the bottom.
Q2.2 For each of the commands marked with *, group them into a shell script to automate execution of the commands.
The script is included here:
#!/bin/bash
# this script redirects the output of a list of commands to a text file
# first clear the terminal window
clear
echo "angelaC.txt" >angelaC.txt
echo "Question 2.2 CATC Assignment">>angelaC.txt
echo >>angelaC.txt
echo "Angela C">>angelaC.txt
# append to text file for the rest of the commands
echo >>angelaC.txt
echo "This text file contains the output of the commands marked by an asterisk for question 2.2 ">>angelaC.txt
echo >>angelaC.txt
echo "you can view the text file by using cat command as follows: cat angelaC.txt"
echo >>angelaC.txt
echo "the following list of commands are executed and their output redirected to angelaC.txt" >>angelaC.txt
echo "date, hostname, uptime, arch, uname -a, uptime, whoami, who, finger, w, top and history " >>angelaC.txt
echo >>angelaC.txt
echo >>angelaC.txt
echo -n "date command shows the current system, date and time: " >>angelaC.txt
echo >>angelaC.txt
date >>angelaC.txt
echo >>angelaC.txt
echo -n "Hostname shows the current host system is ">>angelaC.txt
echo >>angelaC.txt
hostname >>angelaC.txt
echo -n "Arch commands shows the machines hardware architecture type is ">>angelaC.txt
arch >>angelaC.txt
echo >>angelaC.txt
echo "Uname - a shows some system information including the kernel name, the network node hostname, the release version number, the kernel version, the machine hardware name, the processor type, the hardware platform and the operating system " >>angelaC.txt
echo >>angelaC.txt
uname -a >>angelaC.txt
echo >>angelaC.txt
echo -n "Uptime shows that the system has been up and running for the following number of days, hours and minutes " >>angelaC.txt
uptime>>angelaC.txt
echo >>angelaC.txt
echo -n "Whoami - The username of the user running the commands is " >>angelaC.txt
whoami >>angelaC.txt
echo >>angelaC.txt
echo "Who command shows the names of the users who are currently logged in : ">>angelaC.txt
echo >>angelaC.txt
who>>angelaC.txt
echo >>angelaC.txt
echo "Finger command shows some information about the system users " >>angelaC.txt
echo >>angelaC.txt
finger >>angelaC.txt
echo >>angelaC.txt
echo "w - shows the current activity on the machine - who is logged in and what they are doing">>angelaC.txt
echo >>angelaC.txt
w >>angelaC.txt
echo >>angelaC.txt
echo "top command shows the linux commands that are currently running and some system information about them" >>angelaC.txt
echo >>angelaC.txt
echo "Note - you may need to press q to quit from the top command "
top >>angelaC.txt
echo >> angelaC.txt
echo "and finally the output of the history command " >>angelaC.txt
history >> angelaC.txt
echo "thats all for now - the output of the commands has been directed to angelaC.txt"
echo " Note that you can see the text file created from running this program by entering cat angelaC.txt"
echo " you can also use the head and tail commands to see just the start and the finish of the file "
echo "goodbye"
Other parts of this linux assignment involved changing the access permissions using the chmod command so that your your personal folder is fully accessible to you (read, write and execute privileges) and totally inaccessible to the group and all other users.
Also using the ‘Lynx’ text-based browser installed on the VM to search for an online IP address location service to determine the city and country where the VM is located.
Because there is no GUI installed on the VM, all programs have to run instead in text mode.
To run the Lynx text-based browser type lynx www.google.com.
Q2.4 Write a shell script that behaves like an Irish person offering a cup of tea.
#!/bin/bash
# A shell script that acts like an Irish person offering a cup of tea.
# My submission as part of the CATC module project.
# initialise num for the while loop
num=1
# ask question and read answer into 'ans'
read -p "would you like a cup of tea? " ans
# if answer is no, ask again 4 more times max, but less if the answer is yes
if [ $ans == "n" ] || [ $ans == "no" ] || [ $ans == "N" ] || [ $ans == "NO" ]; then
# echo "what a pity "
# start a while loop that will run max 4 times
while [ $num -le 4 ]; do
# ask again and read answer into 'ans2'
read -p "Are you sure? " ans2
# increment the num variable to prevent loop running forever
num=$((num + 1))
# if the answer has changed to a yes answer, then make the tea
if [ $ans2 == "y" ] || [ $ans2 == 'yes' ] || [ $ans2 == "Y" ]; then
echo "Great, I'll make tea now"
# otherwise, after asking 4 more times the loop ends
break
#close if statement
fi
# close while loop
done
# if answer to initial question was yes, just make the tea
elif [ $ans == "y" ] || [ $ans == "yes" ] || [ $ans == "Y" ] || [ $ans == "Yes" ]; then
echo "Great, I'll make tea now"
else
echo "Sorry, I don't quite understand. Too bad!"
fi
